Greetings! I'm Aneesh Sreedharan, CEO of 2Hats Logic Solutions. At 2Hats Logic Solutions, we are dedicated to providing technical expertise and resolving your concerns in the world of technology. Our blog page serves as a resource where we share insights and experiences, offering valuable perspectives on your queries.

Introduction to Web Application Security Testing
How safe are your online transactions?
With cybercriminals constantly seeking vulnerabilities in web applications, the risks to your sensitive information are ever-present. One exploit can lead to significant data breaches, leaving businesses and users vulnerable.
That’s where web application security testing becomes essential. By systematically identifying and mitigating security risks, organizations can secure their defenses. As businesses increasingly embrace DevOps methodologies, integrating automation into security testing processes is crucial for maintaining continuous protection against evolving threats.
In this blog, we will explore how automating web application security testing can enhance security measures in the DevOps framework.
Understanding DevOps in the Security Context
DevOps is a collaborative approach that integrates development and operations to increase the speed and reliability of software delivery. In a security context, often referred to as DevSecOps, this approach ensures that security practices are embedded throughout the software development lifecycle (SDLC). As a result, organizations can proactively address security risks without compromising the efficiency and agility of the DevOps process.
8 Benefits of Automating Security Testing
Take a look at how automating security testing can help development process:
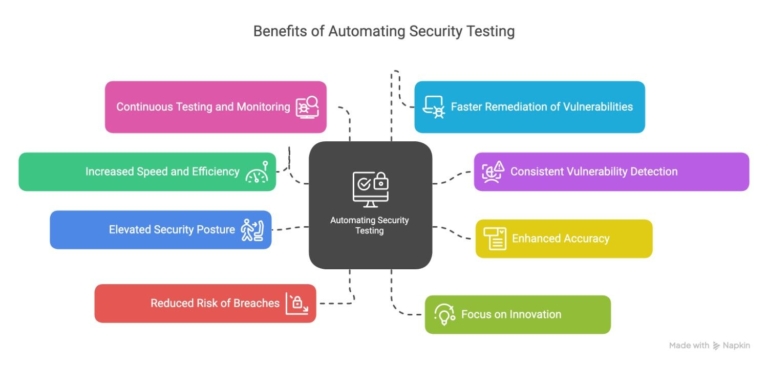
- Increased Speed and Efficiency: Automation significantly accelerates the security testing process, allowing for quicker deployment of web applications.
- Consistent Vulnerability Detection: Automated tools provide uniform assessments, leading to reliable identification of vulnerabilities across various environments.
- Enhanced Accuracy: Automation reduces human error, ensuring more accurate identification of potential threats and weaknesses.
- Elevated Security Posture: Integrating automated web security tools under the DevOps system enhances the general security system.
- Reduced Risk of Breaches: Reduce the chances of cyber attacks by identifying such vulnerabilities early, and identifying methods of addressing them.
- Focus on Innovation: Developers can concentrate on delivering new features and innovations rather than spending time on manual testing processes.
- Continuous Testing and Monitoring: Automation allows continual security evaluation and, thus rapid response to new risks.
- Faster Remediation of Vulnerabilities: Immediate identification of security issues allows for quicker fixes, enhancing the overall security outcome.
Types of Automated Security Testing Tools
The two main categories of automated security testing tools are those that focus on code-related security and those that target server-related security. Both possess great potential for identifying and preventing vulnerabilities. Here, we’ll outline specific tools that can help in identifying these issues efficiently.
Code-Related Security Issues
- Injection Attacks: To make sure that the inputs are verified, automated technologies such as Static Application Security Testing (SAST) tools will scan the source code for any injection vulnerabilities.
- Cross-Site Scripting (XSS): Dynamic Application Security Testing (DAST) tools simulate real-world attacks on running applications to identify XSS vulnerabilities and suggest fixes.
- Buffer Overflows: Static Analysis tools can catch improper handling of buffer sizes, leading to overflows, allowing developers to correct them in the earlier stages.
- Misconfigurations: Tools like Software Composition Analysis (SCA) scan for outdated libraries or APIs and flag potential misconfigurations before they can be exploited.
- Business Logic Flaws: Automated testing frameworks can simulate user interactions and workflows to identify improper authentication and authorization flaws.
Server-Related Security Issues
- Server Misconfigurations: Certain technologies perform an automatic check of server configurations about security baselines. This makes it possible to quickly address and remedy vulnerabilities and unpatched software.
- Network Security Flaws: By identifying vulnerabilities in a network setup, such as unprotected ports and inadequate encryption, scanning tools can assist fortify the network’s defenses against intrusions.
- Storage & OS-Level Vulnerabilities: To ensure the security of the operating systems and storage, automated methods scan for rootkits and evaluate encryption techniques on data.
Implementing Automated Security Testing in DevOps Pipelines
To implement automated security testing effectively in DevOps pipelines, follow these steps:
Step 1: Ensure that security is considered throughout the Software Development Life Cycle (SDLC).
Step 2: Incorporate Static Application Security Testing (SAST)
- Utilize SAST tools like Codacy while coding.
- Examine the source code to find security holes before implementation.
Step 3: Utilize Dynamic Application Security Testing (DAST)
- Throughout the testing stage, implement DAST tools like WAF.
- To find vulnerabilities while the application is operating, do real-time testing.
Step 4: Implement Continuous Monitoring Solutions
- Incorporate monitoring tools like Amazon Cloudwatch while the system is being deployed.
- Continuously assess the application for security threats in real-time.
Step 5: Establish a Stepwise Integration Approach
- To improve the security posture gradually, use a phased implementation.
- Make sure vulnerabilities are found early during the development process.
Step 6: Conduct Regular Security Reviews
- Review and update security procedures and tools regularly.
- Adapt to new threats and update security measures accordingly.
Companies can add strong automated security testing to their DevOps pipelines and guarantee ongoing vulnerability protection by taking these actions.
Best Practices for Automation in Security Testing
To optimize the advantages of security testing automation, companies ought to implement optimal methodologies like:
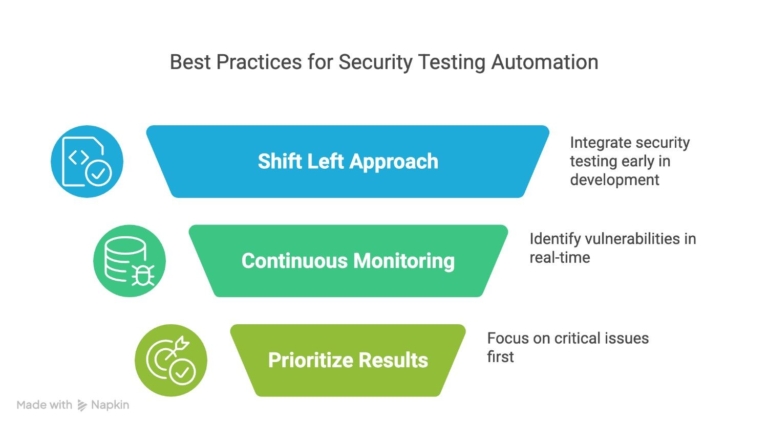
- Shift Left Approach: Make sure that early on in the development process, security testing is conducted. Vulnerabilities can be quickly identified and fixed in this way.
- Continuous Monitoring: Make use of automated technologies to periodically evaluate the servers’ and applications’ security.
- Sorting the Results by Priority: Pay close attention to the most serious vulnerabilities initially to make sure that they are fixed as soon as possible.
Challenges in Automating Security Testing
Automating security testing offers significant advantages, but it also presents some challenges that businesses must address to ensure success. Key drawbacks include:
- Managing and controlling tool outputs can be challenging.
- Integrating automated security testing with existing tools requires effort.
- Ensuring comprehensive coverage across diverse environments is difficult.
- Automation techniques need continuous improvement to remain effective.
- Balancing automation with manual testing is necessary for thorough results.
Conclusion
When integrating security testing into web applications, you must adopt the advancement of DevOps automation. Are you prepared to enhance your security posture and streamline your development processes? Connect with a DevOps consultancy to enhance security with automated testing tools for operational efficiency.
Table of contents
- Introduction to Web Application Security Testing
- Understanding DevOps in the Security Context
- Benefits of Automating Security Testing
- Types of Automated Security Testing Tools
- Implementing Automated Security Testing in DevOps Pipelines
- Best Practices for Automation in Security Testing
- Challenges in Automating Security Testing

Related Articles







